Cybersecurity has become a core business function. Every organisation now relies on digital infrastructure, distributed teams and interconnected applications to operate. With that dependency comes a simple truth: the systems we build evolve faster than the controls that protect them. In this environment, vulnerability scanning is no longer a periodic task. It is the foundation of any credible defence.
When done well, vulnerability scanning reveals where systems are exposed, how risk moves through an organisation and which weaknesses require attention first. This article explores why vulnerability scanning matters more than ever and how it fits into a modern approach to proactive security.
Why Vulnerability Scanning Matters More Than Ever
The threat landscape is not only expanding. It is accelerating. Attackers move quickly, often using automation and AI to identify weaknesses faster than humans can respond. Vulnerability scanning gives organisations a way to see their exposure before attackers do.
An Expanding Attack Surface
Cloud adoption, remote access, API driven architectures and third party services have multiplied the number of places where vulnerabilities can appear. Scanning helps teams map this surface and understand which assets require urgent protection.
The Rise of Zero Day Exploits
Zero day vulnerabilities are increasing in frequency and impact. Scanning tools cannot detect an unknown flaw directly, but they can surface insecure configurations, design weaknesses and attack pathways that commonly enable successful zero day exploitation. Reducing these weaknesses significantly limits the blast radius of zero days.
Growing Compliance Expectations
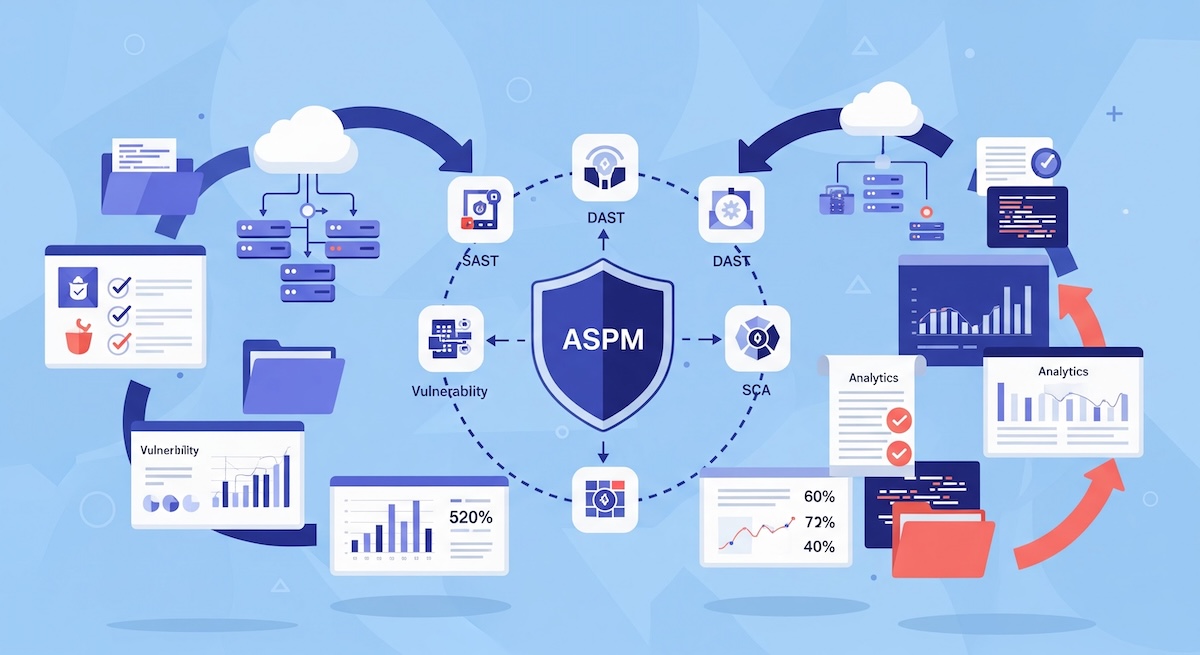
Regulatory frameworks such as ISO 27001, SOC 2 and the Cyber Resilience Act expect organisations to demonstrate continuous control over their security posture. Regular vulnerability scanning is often a required control. Platforms like ScanDog simplify compliance by offering traceable evidence and mapped controls within its Application Security Posture Management framework.
A Shift Toward Proactive Security
Reactive security is no longer sustainable. Vulnerability scanning allows organisations to move into a preventive mindset by addressing weaknesses long before they become incidents.
How Vulnerability Scanning Works
At its core, vulnerability scanning compares systems, applications and infrastructure against known weaknesses. It highlights misconfigurations, outdated components, exposed services and insecure settings. Yet scanning has evolved significantly.
Key Components of Effective Vulnerability Scanning
Regular scanning
Frequent scans capture new vulnerabilities as they appear.
Risk based prioritisation
Not all findings matter equally. Scans must be paired with context to determine what requires action. ScanDog’s contextual prioritisation plays a role here by evaluating exploitability, reachability and business impact.
Continuous monitoring
Modern environments change by the hour. Continuous scanning helps maintain an accurate posture.
Integration into development pipelines
Embedding scanning into CI/CD workflows ensures vulnerabilities are caught before they reach production.
Vulnerability Scanning in 2024: What Has Changed
As architectures evolve, scanning must evolve with them. The landscape now includes cloud resources, containers, microservices and ephemeral workloads. Each brings new challenges and demands deeper visibility.
Cloud and Container Scanning
Cloud environments introduce configuration drift and complex privilege boundaries. Containers and Kubernetes clusters shift constantly. Modern scanners assess these environments continuously.
AI Driven Vulnerability Detection
AI helps identify anomalies, suspicious behaviour and patterns that traditional scanners might miss. It helps reduce false positives and highlights issues that require immediate attention.
Automated Remediation
Some platforms now assist with suggesting code fixes. This improves response times and reduces the workload on security and engineering teams. ScanDog contributes to this shift with automated pull request creation, keeping a human-in-the-loop and hence allowing developers to apply verified remediations safely.
Integration Across the Security Ecosystem
Vulnerability scanning tools increasingly connect with SIEM, SOAR and threat intelligence systems. This integration improves detection, speeds up response and enriches analysis.
Challenges in Vulnerability Scanning
Even with strong tools, vulnerability scanning brings its own set of challenges.
False Positives and False Negatives
Scanners sometimes report issues that are not exploitable or miss issues that are. AI and behavioural analysis help reduce this, but human oversight remains essential.
Prioritisation Difficulties
Large organisations often receive thousands of findings. Without context, prioritisation becomes overwhelming. This is where ASPM solutions such as ScanDog provide significant value by focusing attention on issues that truly introduce critical risk.
Complex IT Environments
Hybrid cloud environments, legacy systems and distributed architectures require scanners that are flexible and continuously updated. Ensuring coverage across all assets is a constant challenge.
Moving Forward With Confidence: Why Vulnerability Scanning Remains Foundational
Vulnerability scanning remains one of the most effective ways to reduce risk. It offers visibility, clarity and a pathway to making informed decisions in a world where threats evolve daily.
Organisations that combine continuous scanning with contextual prioritisation and guided remediation gain a powerful advantage. ScanDog supports this modern approach by orchestrating multiple scanners, enriching findings with contextual intelligence and helping teams remediate vulnerabilities efficiently.
In the broader cybersecurity landscape, vulnerability scanning is no longer optional. It is the discipline that allows organisations to stay resilient, adapt quickly and build systems that can withstand the pressures of the modern threat environment.
ScanDog is an AI-powered Application Security Posture Management (ASPM) platform that helps development teams build secure software faster. With advanced vulnerability prioritization, reachability analysis, and AI-assisted remediation, ScanDog cuts through the noise of false positives to focus on what truly matters.