Modern software development depends on an enormous ecosystem of open source libraries. This brings remarkable speed and innovation, but also introduces risk that is difficult to track manually. Software Composition Analysis , SCA , has become the standard way to understand vulnerabilities in these dependencies. Yet for many teams, SCA brings a familiar problem. Too many alerts. Too little context. And far too many false positives.
Dependency scanning works best when it helps developers understand which vulnerabilities truly matter. But without deeper insight, traditional SCA often highlights risks that are not exploitable, not reachable and not relevant. It creates noise rather than clarity.
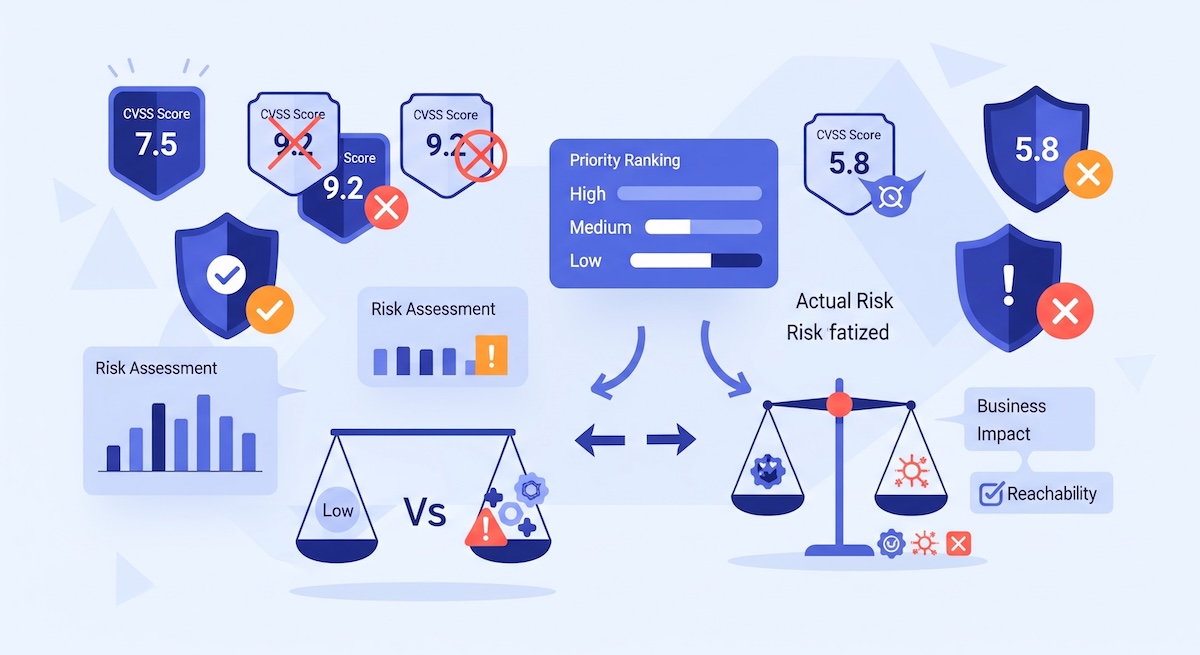
This is where reachability transforms the conversation. And it is where modern platforms, including ScanDog, use reachability to strengthen signal quality and rebuild trust between AppSec and engineering.
What Reachability Means in SCA
Reachability analysis asks a simple but crucial question.
Does your application actually call the vulnerable function inside the dependency?
SCA alone will detect that a library contains a vulnerability. Reachability determines whether that vulnerable code path can actually be executed in your environment.
How it works
SCA detects a vulnerable dependency.
It flags a CVE present in a package or version.
Reachability analyses real code paths.
It examines your call graph to see whether your application ever invokes the vulnerable method.
If the method is never used, the risk changes entirely.
A non reachable vulnerability still deserves attention, but it no longer demands urgency.
This additional layer of context dramatically reduces false positives, especially in large projects with deep or nested dependency trees.
The False Positive Problem in Dependency Scanning
False positives are the greatest barrier to effective SCA adoption. They reduce trust, delay remediation and create unnecessary friction between security and engineering.
Why SCA produces so many false positives
Dependency chains are deep and complex.
Most applications include libraries with hundreds of functions, only a few of which are ever used.
SCA tools focus on package level vulnerabilities.
They rarely understand whether your application reaches the vulnerable code path.
Developers become desensitised to alerts.
When findings lack context, they are more likely to be ignored.
What the data shows
Research from multiple industry reports highlights the scale of the issue.
Up to 95% of SCA findings are not exploitable because the vulnerable function is never invoked.
Most engineers say false positives lower productivity and slow remediation.
Many teams prefer fewer accurate findings over more frequent alerts.
This is not simply a tooling issue. It is a context issue. And reachability is the missing context.
How Reachability Improves SCA Accuracy
Reachability transforms SCA from a long list of theoretical vulnerabilities into a focused view of actual risk.
Without reachability
Every vulnerability is treated the same, regardless of whether it can be exploited.
With reachability
Findings are sorted by whether they are reachable, exploitable or meaningful in your architecture.
Why this matters
- Fewer false positives
- Better signal to noise ratio
- Faster remediation cycles
- Stronger trust between developers and security teams
When developers see findings that consistently align with real risk, they respond faster and with more confidence.
How ScanDog Strengthens SCA With Reachability
ScanDog extends traditional SCA by adding contextual intelligence, call graph analysis and dependency usage mapping. This makes SCA findings both more accurate and more actionable.
Key enhancements ScanDog provides
Correlates SCA findings with real code paths
Shows whether the application reaches the vulnerable function.
Detects reachable vulnerable methods across services
Helping teams understand true exploitability.
Visualises dependency usage
Clear visibility into where and how libraries are used within a system.
Generates remediation tickets only for exploitable findings
Avoiding unnecessary work and reducing developer fatigue.
Integrates SCA insights into the broader ASPM posture
Connecting dependency scanning with SAST, IaC and runtime analysis.
More details can be found on the ScanDog ASPM page.
Ecosystem coverage
ScanDog supports workflows across GitHub, GitLab and Azure DevOps and works with languages such as JavaScript, Go, Rust, Java, Python, C and C plus plus. The platform integrates with popular scanners including Snyk, Trivy, Grype and OWASP depscan.
This creates a single, clear view of dependency risk that replaces the overwhelming noise of traditional SCA.
Why Reachability Is Becoming Essential for Modern AppSec
SCA without reachability is like receiving a weather warning for a region you do not live in. It may be accurate in the abstract, but it is not meaningful for you. Reachability turns theoretical risk into real risk and gives teams the confidence to act where it matters most.
As applications grow more distributed and dependencies more complex, reachability is becoming central to effective AppSec and a key mechanism for reducing false positives at scale.
Platforms such as ScanDog help teams turn SCA into something actionable, contextual and trustworthy by embedding reachability into the heart of dependency scanning.
ScanDog is an AI-powered Application Security Posture Management (ASPM) platform that helps development teams build secure software faster. With advanced vulnerability prioritization, reachability analysis, and AI-assisted remediation, ScanDog cuts through the noise of false positives to focus on what truly matters.