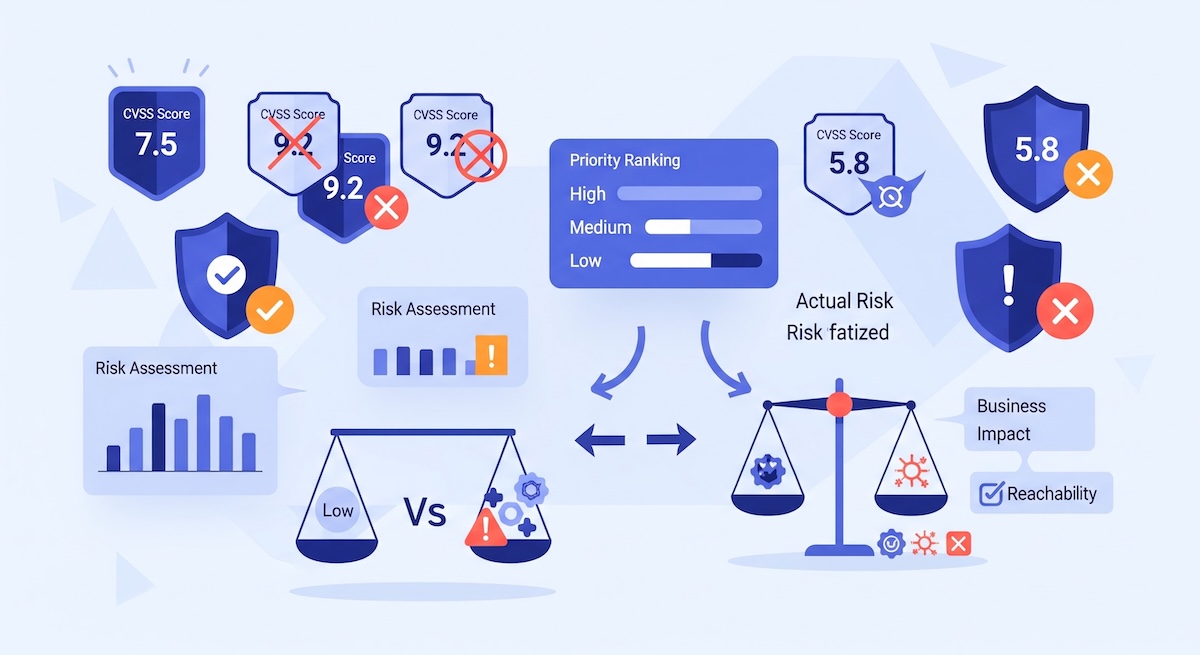
When it comes to vulnerability management, organizations often fall into the trap of relying solely on severity ratings or CVSS scores to determine which issues to address first. While these scores provide a standardized way to measure the impact of a vulnerability, they lack the context needed to make informed risk-based decisions. In today’s dynamic threat landscape, effective vulnerability management requires a smarter approach—one that aligns remediation efforts with business impact, exploitability, and organizational risk. This is where true vulnerability prioritization comes into play.
The Pitfalls of Focusing Solely on CVSS Scores
CVSS (Common Vulnerability Scoring System) is a widely used framework for measuring the severity of vulnerabilities, but it has significant limitations:
- Lack of Business Context: CVSS scores don’t account for how critical an affected system is to business operations.
- No Consideration for Exploitability: Not all vulnerabilities with high CVSS scores are actively exploited in the wild, making some a lower priority than others.
- Overwhelming Volume: Security teams are flooded with high-severity vulnerabilities, leading to alert fatigue and inefficient patching strategies.
- Static Scoring Model: CVSS does not adjust dynamically based on real-world threats, such as active exploitation or ransomware targeting.
Why Prioritization Matters More Than Severity
Rather than treating all high-severity vulnerabilities as equal, organizations should prioritize remediation efforts based on real-world risk. A robust vulnerability prioritization strategy should consider the following factors:
- Exploitability: Is the vulnerability being actively exploited in the wild? Is there public exploit code available?
- Business Impact: Does the affected asset support critical business operations? Will an exploit cause operational downtime or financial loss?
- Asset Exposure: Is the system internet-facing or internal? Are there compensating controls in place to mitigate risk?
- Threat Intelligence: Are there reports of this vulnerability being used in targeted attacks or ransomware campaigns?
- Fix Complexity: How difficult is it to apply a fix? Is there a risk of breaking production systems?
ScanDog’s Approach to Smarter Vulnerability Management
At ScanDog.io, we go beyond basic CVSS scores to provide a truly risk-based approach to vulnerability management. Our platform enables organizations to:
- Leverage Real-Time Threat Intelligence: We continuously monitor exploit data and threat actor activity to highlight vulnerabilities that pose an immediate risk.
- Prioritize Based on Business Context: ScanDog helps organizations align remediation efforts with their unique business-critical assets, reducing unnecessary patching efforts.
- Incorporate Fix Complexity and Operational Impact: Instead of just flagging vulnerabilities, we assess how feasible it is to implement fixes without disrupting workflows.
- Automate and Streamline Decision-Making: Our intelligent workflows ensure that security teams focus on what truly matters, improving remediation efficiency and reducing risk exposure.
The Future of Vulnerability Management
Security teams need to shift their mindset from “patch everything with a high CVSS score” to “fix what truly matters first.” By integrating business context, exploitability, and risk factors into their vulnerability management strategy, organizations can improve security outcomes without wasting resources on low-priority threats.
Conclusion
By prioritizing vulnerabilities based on real-world risk, organizations can improve security outcomes without wasting resources on low-priority threats. This is where true vulnerability prioritization comes into play. ScanDog.io is designed to help organizations make this shift. If you’re ready to move beyond outdated vulnerability scoring models and adopt a smarter, risk-driven approach, get in touch with us today.
Call-to-Action:
Ready to revolutionize your vulnerability management? Contact Us today or Start Now to see how we help security teams prioritize vulnerabilities with precision.