On September 8, 2025, attackers slipped malicious code into some of the most widely used npm packages — including chalk, debug, ansi-regex, and others with billions of downloads each month.
The payload was designed to run in browsers, quietly intercepting crypto wallet data and even rewriting transactions to redirect funds. For a few hours, compromised versions were live on npm — long enough to make their way into build pipelines, production bundles, and potentially end-user environments.
This wasn’t a theoretical risk. It was fast, widespread, and deeply embedded in the libraries developers use every day for logging, debugging, and formatting output.
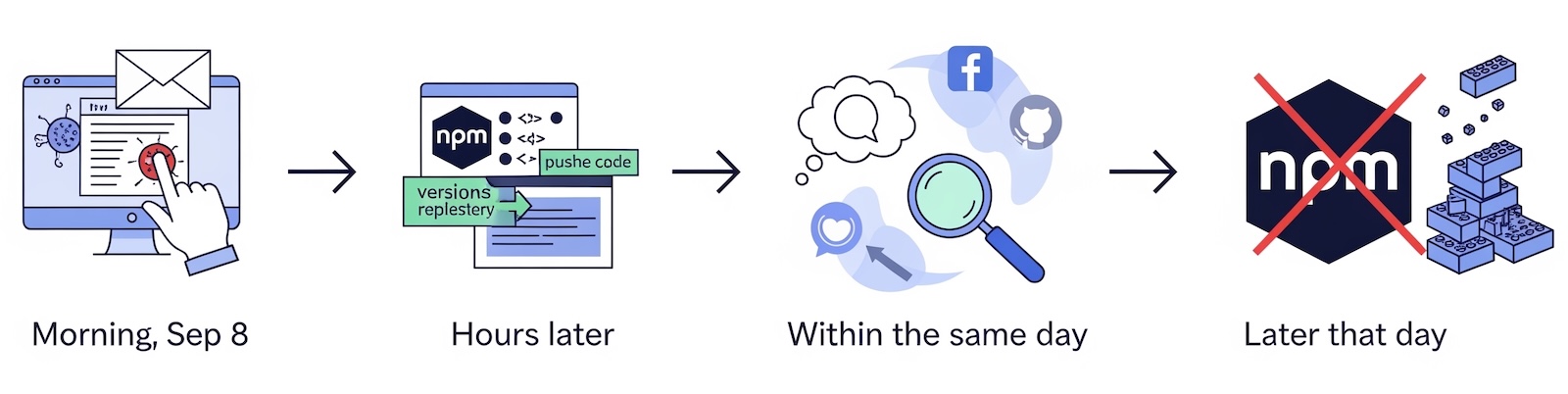
🕒 Timeline at a Glance
- Morning, Sep 8 – A maintainer’s npm account is phished.
- Hours later – Malicious versions are published to npm, replacing trusted releases.
- Within the same day – Security researchers notice suspicious behavior; reports spread across GitHub and social media.
- Later that day – npm security and maintainers remove the compromised versions, but by then, many projects may have already pulled them into builds.
What the Malicious Code Did
Researchers who de-obfuscated the payload revealed it acted as a browser/web3 interceptor.
When the compromised code made its way into frontend bundles and loaded in a browser, it:
- Hooked wallet- and network-related APIs
- Silently rewrote transaction recipients and approvals so funds could be diverted to attacker wallets
- Exfiltrated wallet data for later abuse
Notably, the malware stayed dormant in Node.js environments and only executed in browser contexts — making the compromise of UI/output libraries especially dangerous.
Confirmed Malicious Package Versions
Security teams have published a list of known-bad versions.
If any of these appear in your lockfiles, SBOMs, or deployed bundles, treat them as compromised:
chalk — 5.6.1
chalk-template — 1.1.1
ansi-regex — 6.2.1
strip-ansi — 7.1.1
wrap-ansi — 9.0.1
slice-ansi — 7.1.1
ansi-styles — 6.2.2
supports-color — 10.2.1
supports-hyperlinks — 4.1.1
has-ansi — 6.0.1
debug — 4.4.2
color-convert — 3.1.1
color-name — 2.0.1
color — 5.0.1
color-string — 2.1.1
simple-swizzle — 0.2.3
is-arrayish — 0.3.3
backslash — 0.2.1Additional indicators and rules are available from security vendors including Semgrep and StepSecurity.
Am I Affected? Quick Checks to Run
-
Search your repo/CI artifacts for the exact versions
grep -R "[email protected]" package-lock.json yarn.lock node_modules -n || truenpm ls [email protected] || true- For monorepos:
grep -R -E "chalk.*5\.6\.1|debug.*4\.4\.2" . -n || true
-
Generate an SBOM and scan it
syft . -o json > sbom.jsongrype sbom:sbom.json- (Snyk, Sonatype, and Semgrep have also published rules for detection.)
-
Check built frontend bundles (critical!)
- The malicious payload was designed to run in browsers.
- Search your production JS bundles for suspicious references such as:
window.ethereumwallet referencesExact malicious package versions- If these versions were present at build time, assume the shipped bundle may contain the payload.
✅ Quick Checklist: What You Should Do Right Now
- Check your lockfiles & SBOMs for the following versions:
[email protected],[email protected],[email protected], and others from the full list.
- Rebuild from clean environments — don’t rely on cached
node_modules. - Search your deployed bundles (especially front-end apps) for these versions.
- Pause deployments if compromised versions were pulled in.
- Rotate secrets (npm tokens, CI/CD credentials) if they may have been exposed.
If any of these malicious versions appear in your environment, treat it as an incident.
🚨 How ScanDog Helps When the Clock is Ticking
When a supply-chain attack like this hits, the first question is always the same: “Are we exposed?”
With ScanDog, you don’t need to guess.
- Immediate detection: ScanDog scans your repos and CI pipelines against live SCA and SBOM data, flagging the exact malicious versions — automatically.
- Clarity, not noise: Reachability analysis shows whether the compromised code is actually executed in your apps, so you can focus on real risk.
- Automated containment: ScanDog can block bad builds, open tickets in Jira, and ping your Slack channel the moment malicious versions are detected.
- Faster remediation: AI-Fix suggests concrete patches, even generating PRs to replace compromised packages with safe ones — complete with diffs and explanations.
- One dashboard for everything: The Remediation Center keeps track of which repos are affected, who’s fixing them, and what’s already resolved.
Instead of scrambling through lockfiles and Slack threads, ScanDog helps you move from “We might be compromised” to “We’ve contained and fixed it” — in hours, not days.